In this post, I will aim to highlight the various breakout sessions I’ve attended during the day 2 at VMworld 2016 US, key items / notes / points learnt and few other interesting things I was privy to during the day that is worth mentioning, along with my thoughts on them…!!
Day 2 – Breakout Session 1 – Understanding the availability features of VSAN
- Session ID: STO8179R
- Presenters:
- GS Khalsa – Sr. Technical Marketing manager – VMware (@gurusimran)
- Jeff Hunter – Staff Technical Marketing Architect – VMware (@Jhuntervmware)
In all honesty, I wasn’t quite sure why I signed up to this breakout session as I know VSAN fairly well, including its various availability features as I’ve been working with testing & analysing its architecture and performance when VSAN was first launched to then designing and deploying VSAN solutions on behalf of my customers for a while. However, having attended the session it reminded me of a key fact that I normally try to never forget which is “you always learn something new” even when you think you know most of it.
Anyways, about the session itself, it was good and was mainly aimed at the beginners to VSAN but I did manage to learn few new things as well as refresh my memory on few other facts, regarding VSAN architecture. The key new ones I learnt are as follows
- VSAN component statuses (as shown within vSphere Web Client) and their meanings
- Absent
- This means VSAN things the said component will probably return. Examples are,
- Host rebooted
- Disk pulled
- NW partition
- Rebuild starts after 60 mins
- When an item is detected / marked as absent, VSNA typically wait for 60 minutes before a rebuild is started in order to allow temporary failure to rectify itself
- This means for example, pulling disks out of VSAN will NOT trigger an instant rebuild / secondary copy…etc. so it wont be an accurate test of VSAN
- This means VSAN things the said component will probably return. Examples are,
- Degraded
- This typically means the device / component is unlikely to return. Examples include,
- A permeant Device Loss (PDL) or a failed disk
- When a degraded item is noted, a rebuild started immediately
- This typically means the device / component is unlikely to return. Examples include,
- Active-Stale
- This means the device is back online from a failure (i.e. was absent) but the data residing on it are NOT up to date.
- Absent
- VSAN drive degradation monitoring is proactively logged in the following log files
- vmkernel.log indicating LSOM errors
- Dedupe and Compression during drive failures
- During a drive failure, de-duplication and compression (al flash only) is automatically disabled – I didn’t know this before
Day 2 – Breakout Session 2 – How to deploy VMware NSX with Cisco Nexus / UCS Infrastructure
- Session ID: NET8364R
- Presenters:
- Paul Mancuso – Technical Product Manager (VMware)
- Ron Fuller – Staff System Engineer (VMware)
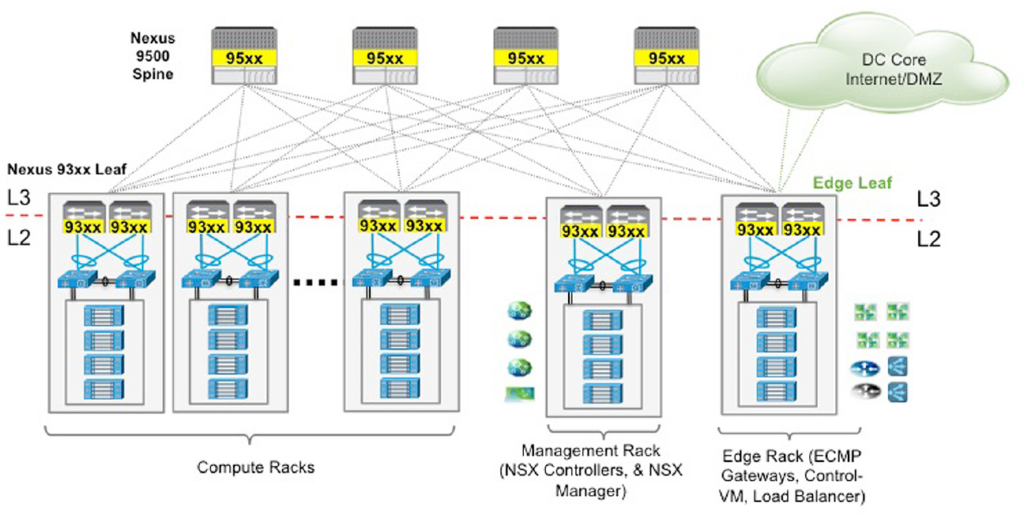
This session was about a deployment architecture for NSX which is becoming increasingly popular, which is about how to design & deploy NSX on top of Cisco Nexus switches with ACI as the underlay network and Cisco UCS hardware. Pretty awesome session and a really popular combination too. (FYI – I’ve been touting that both these solutions are better together since about 2 years back and its really good to see both companies recognising this and now working together on providing guidance stuff like these). Outside of this session I also found out that the Nexus 9k switches will soon have the OVS DB support so that they can be used as TOR switches too with NSX (hardware VTEP to bridge VXLANs to VLANs to communication with physical world), much like the Arista switches with NSX – great great news for the customers indeed.
I’m not going to summarise the content of this session but wold instead like to point people at the following 2 documentation sets from VMware which covers everything that this session was based on, its content and pretty simply, everything you need to know when designing NSX solutions together with Cisco ACI using Nexus 9K switches and Cisco UCS server hardware (blades & rack mounts)
- Design Guide for VMware NSX running with a Cisco ACI Underlay Fabric
- Reference Design: Deploying NSX for vSphere with Cisco UCS and Nexus 9000 Switch Infrastructure
One important thing to keep in mind for all Cisco folks though: Cisco N1K is NOT supported for NSX. All NSX prepped clusters must use vDS. I’m guessing this is very much expected and probably only a commercial decision rather than a technical one.
Personally I am super excited to see VMware ands Cisco are working together again (at least on the outset) when it comes to networking and both companies finally have realised the use cases of ACI and NSX are somewhat complementary to each other (i.e. ACI cannot do most of the clever features NSX is able to deliver in the virtual world, including public clouds and NSX cannot do any of the clever features ACI can offer to a physical fabric). So watch this space for more key joint announcements from both companies…!!
Day 2 – Breakout Session 3 – Containers for the vSphere admin
- Session ID: CNA7522
- Presenters:
- Ryan Kelly – Staff System Engineer (VMware)
A session about how VMware approaches the massive buzz around containerisation through their own vSphere integrated solution (VIC) as well as a brand new hypervisor system designed from ground up with containerisation in mind (Photon platform). This was more of a refresher session for than anything else and I’m not going to summarise all of it but instead, will point you to the dedicated post I’ve written about VMware’s container approach here.
Day 2 – Breakout Session 4 – The architectural future of Network Virtualisation
- Session ID: NET8193R
Presenters: Bruce Davie – CTO, Networking (VMware)
Probably the most inspiring session of the day 2 as Bruce went through the architectural future of NSX where he described what the NSX team within VMware are focusing on as key improvements & advancements of the NSX platform. The summary of the session is as follows
- NSX is the bridge from solving today’s requirement to solving tomorrow’s IT requirements
- Brings remote networking closer easily (i.e. Stretched L2)
- Programtically (read automatically) provisoned on application demand
- Security ingrained at a kernel level and every hop outwards from the applications
- Challenges NSX is trying address (future)
- Developers – Need to rapidly provision and destroy complex networks as a pre-reqs for applications demanded by developers
- Micro services – Container networking ands security
- Containers
- Unseen future requirements
- Current NSX Architecture
- Cloud consumption plane
- Management plane
- Control plane
- Data plane
- Future Architecture – This is what the NSX team is currently looking at for NSX’s future.
- Management plane scale out
- Management plane now needs to be highly available in order to constantly keep taking large number of API calls for action from cloud consumption systems such as OpenStack, vRA..etc – Developer and agile development driven workflows….etc.
- Using & scaling persistent memory for the NSX management layer is also being considered – This is to keep API requests in persistent memory in a scalable way providing write and read scalability & Durability
- Being able to take consistent NSX snapshots – Point in time backups
- Distributed log capability is going to be key in providing this management plane scale out whereby distributed logs that store all the API requests coming from Cloud Consumption Systems will be synchronously stored across multiple nodes providing up to date visibility of the complete state across to all nodes, while also increasing performance due to management node scale out
- Control plane evolution
- Heterogeneity
- Currently vSphere & KVM
- Hyper-V support coming
- Control plane will be split in to 2 layers
- Central control plane
- Local control plane
- Data plane (Hyper-V, vSphere, KVM) specific intelligence
- Heterogeneity
- High performance data plane
- Use the Intel DPDK – A technology that optimize packet processing in Intel CPU
- Packet switching using x86 chips will be the main focus going forward and new technologies such as DPDK will only make this better and better
- DPDK capacities are best placed to optimise iterative processing rather than too many context switching
- NSX has these optimisation code built in to its components
- Use DPDK CPUs in the NSX Edge rack ESXi servers is a potentially good design decision?
- Use the Intel DPDK – A technology that optimize packet processing in Intel CPU
- Management plane scale out
- Possible additional NSX use cases being considered
- NSX for public clouds
- NSX OVS and an agent is deployed to in guest – a technical preview of this solution was demoed by Pat Gelsinger during the opening key note on day 1 of VMworld.
- NSX for containers
- 2 vSwitches
- 1 in guest
- 1 in Hypervisor
- 2 vSwitches
- NSX for public clouds
My thoughts
I like what I heard from the Bruce about the key development focus areas for NSX and looks like all of us, partners & customers of VMware NSX alike, are in for some really cool, business enabling treats from NSX going forward, which kind of reminds me of when vSphere first came out about 20 years ago :-). I am extremely excited about the opportunities NSX present to remove what is often the biggest bottleneck enterprise or corporate IT teams have to overcome to simply get things done quickly and that is the legacy network they have. Networks in most organisations are still very much managed by an old school minded, networking team that do not necessarily understand the convergence of networking with other silos in the data center such as storage and compute, and most importantly when it comes to convergence with modern day applications. It is a fact that software defined networking will bring the efficiency to the networking the way vSphere brought efficiency to compute (want examples how this SDN efficiency is playing today? Look at AWS and Azure as the 2 biggest use cases) where the ability to spin up infrastructure, along with a “virtual” networking layer significantly increases the convenience for the businesses to consume IT (no waiting around for weeks for your networking team to set up new switches with some new VLANs…etc.) as well as significantly decreasing the go to market time for those businesses when it comes to launching new products / money making opportunities. All in all, NSX will act as a key enabler for any business, regardless of the size to have an agile approach to IT and even embrace cloud platforms.
From my perspective, NSX will provide the same, public cloud inspired advantages to customers own data center and not only that but it will go a step further by effectively converting your WAN to an extended LAN by bridging your LAN with a remote network / data center / Public cloud platform to create something like a LAN/WAN (Read LAN over WAN – Trade mark belongs to me :-))which can automatically get deployed, secured (encryption) while also being very application centric (read “App developers can request networking configuration through an API as a part of the app provisioning stage which can automatically apply all the networking settings including creating various networking segments, routing in between & the firewall requirements…etc. Such networking can be provisioned all the way from a container instance where part of the app is running (i.e. DB server instance as a container service) to a public cloud platform which host the other parts (i.e. Web servers).
I’ve always believed that the NSX solution offering is going to be hugely powerful given its various applications and use cases and natural evolution of the NSX platform through the focus areas like those mentioned above will only make it an absolute must have for all customers, in my humble view.
Day 2 – Meeting with Pat Gelsinger and Q&A’s during the exclusive vExpert gathering
As interesting as the breakout sessions during the day have been, this was by far the most significant couple of hours for me on the day. As a #vExpert, I was invited to an off site, vExpert only gathering held at Vegas Mob Museum which happened to include VMware CEO, Pat Gelsinger as the guest of honour. Big thanks to the VMware community team lead by Corey Romero (@vCommunityGuy) for organising this event.
This was an intimate gathering for about 80-100 VMware vExperts who were present at VMworld to meet up at an off site venue and discuss things and also to give everyone a chance to meet with VMware CEO and ask him direct questions, which is something you wouldn’t normally get as an ordinary person so it was pretty good. Pat was pretty awesome as he gave a quick speech about the importance of vExpert community to VMware followed up by a Q&A session where we all had a chance to ask him questions on various fronts. I myself started the Q&A session by asking him the obvious question, “What would be the real impact on VMware once the Dell-EMC merger completes” and Pats answer was pretty straight forward. As Michael Dell (who happened to come on stage during the opening day key note speech said it himself), Dell is pretty impressed with the large ecosystem of VMware partners (most of whom are Dell competitors) and will keep that ecosystem intact going forward and Pat echoed the same message, while also hinting that Dell hardware will play a key role in all VMware product integrations, including using Dell HW by default in most pre-validated and hyper-converged solution offerings going forward, such as using Dell rack mount servers in VCE solutions….etc. (in Pat’s view, Cisco will still play a big role in blade based VCE solution offerings and they are unlikely to walk away from it all just because of Dell integration given the substantial size of revenue that business brings to Cisco).
If I read in between the lines correctly (may be incorrect interpretations from my end here), he also alluded that the real catch of the EMC acquisition as far as Dell was concerned was VMware. Pat explained that most of the financing charges behind the capital raised by Dell will need to be paid through EMC business’s annual run rate revenue (which by the way is roughly the same as the financing interest) so in a way, Dell received VMware for free and given their large ecosystem of partners all contributing towards VMware’s revenue, it is very likely Dell will continue to let VMware run as an independent entity.
There were other interesting questions from the audience and some of the key points made by Pat in answering those questions were,
- VMware are fully committed to increasing NSX adoption by customers and sees NSX as a key revenue generator due to what it brings to the table – I agree 100%
- VMware are working on the ability to provide networking customers through NSX, a capability similar to VMotion for compute as one of their (NSX business units) key goals. Pat mentioned that engineering in fact have this figured out already and testing internally but not quite production ready.
- In relation to VMware’s Cross Cloud Services as a service offering (announced by Pat during the event opening keynote speech), VMware are also working on offering NSX as a service – Though the detail were not discussed, I’m guessing this would be through the IBM and vCAN partners
- Hinted that a major announcement on the VMware Photon platform (One of the VMware vSphere container solutions) will be taking place during VMworld Barcelona – I’ve heard the same from the BU’s engineers too and look forward to Barcelona announcements
- VMware’s own cloud platform, vCloud air WILL continue to stay focused on targeted use cases while the future scale of VMware’s cloud business will be expected to come from the vCAN partners (hosting providers that use VMware technologies and as a result are part of the VMware vCloud Air Network…i.e IBM)
- Pat also mentioned about the focus VMware will have on IOT and to this effect, he mentioned about the custom IOT solution VMware have already built or working on (I cannot quite remember which was it) for monitoring health devices through the Android platform – I’m guessing this is through their project ICE and LIOTA (Little IOT Agent) platform which already had similar device monitoring solutions being demoed in the solutions exchange during VMworld 2016. I mentioned about that during my previous post here
It was really good to have had the chance to listen to Pat up close and be able to ask direct questions and get frank answers which was a fine way to end a productive and an education day for me at VMworld 2016 US
Image credit goes to VMware..!!
Cheers
Chan