I came across this weird issue on vRA 6.2.1 where, during the IaaS blueprint creation, most of the actions that should be available (such as “power on”, “Reboot”, “Suspend”…etc.) were not available to be allocated to catalog items (blueprints & services). All of these actions are supposed to be IaaS catalog actions that are available by default once the IaaS components have been deployed, that you can assign to business groups / users when blueprints / catalog items are entitled to users, so that once a vm / server has been provisioned from the said blueprints, those actions are available to the users to interact with the vm / server, through the vRA web portal. If you had this issue, when you login to the vRA portal with tenant administrator privileges, all the actions shown below where the source is listed as IaaS were missing (Everything outside of the highlighted actions below were missing)
This has always been a known issue with previous versions of vCAC where the recommended fix was to run the following command on the IaaS web server, as an administrator.
C:\Program Files (x86)\VMware\vCAC\Server\Model Manager Data\Cafe\Vcac-Config.exe registercatalogtypes -v
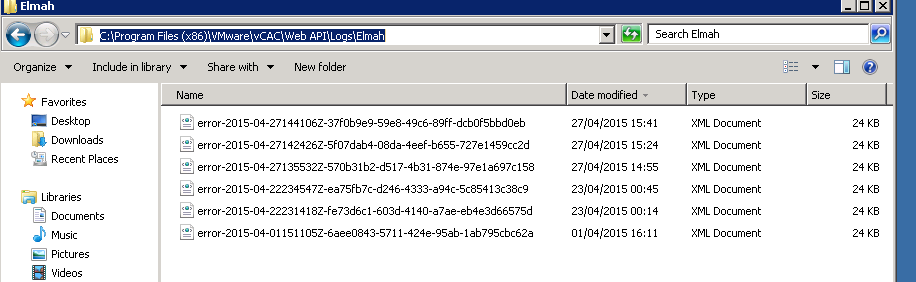
However, with vRA 6.2.x platform (specifically, version 6.2.1), I found that this command alone wouldn’t fix the problem. In my environment, running the above command comes back as succeeded but the actions were still not available. Having raised a VMware support ticket, it turned out that the SAML Token Validation Check (enforced through a configuration line item in C:\Program Files (x86)\VMware\vCAC\Web API\Web.Config file on the IaaS server) is also failing which needs to be fixed as well. If you have the same issue of missing actions in your vRA setup and running the above command doesn’t fix the issue on the vRA 6.2 platform, check the C:\Program Files (x86)\VMware\vCAC\Web API\Logs\Elmah directory on the IaaS server and check if you can see a number of XML files as follows
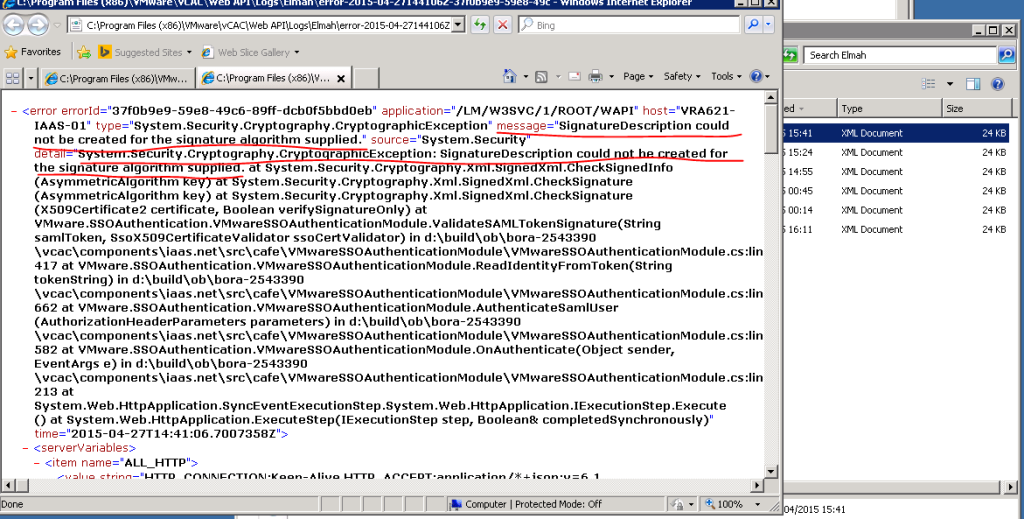
If you see them, open the most recent one up and check for the lines highlighted below
If this is the case, this is a known issue with regards to the vRA 6.2 platform, internally within VMware and currently there is no specific KB article related to this. From what I found out through VMware support, the issue is caused by vRA sending a signature that is using an algorithm not compatible wit the .Net code on the IaaS server and the error is seen in the Elmah XML file (above), that states “System.Security.Cryptography.CryptographicException: SignatureDescription could not be created for the signature algorithm supplied“. While a formal fix is likely going to be included in a future release, currently there’s only a workaround available which is to amend the web.Config file to disable SAML Token validation Check. Heres what you need to do.
- Go to the IaaS web server as an Administrator and backup the current C:\Program Files (x86)\VMware\vCAC\Web API\Web.Config file (I’d cope & rename this as Web.Config.Backup
- Open notepad as Administrator and open the original Web.Config and replace the <!– add key=”DisableSAMLTokenSignatureCheck” value=”false”–> with <add key=”DisableSAMLTokenSignatureCheck” value=”true”/>
- Once replaced, the new Web.Config file should be as follows.

- Now run iisreset to restart IIS and ensure all the vRA services are started back up correctly
- Now (re) run the following command, as an administrator
- C:\Program Files (x86)\VMware\vCAC\Server\Model Manager Data\Cafe\Vcac-Config.exe registercatalogtypes -v
- You will now see the missing actions being available on the vRA to be assigned to the catalog items.
Hope this was useful
Cheers
Chan